Notebook Security
The Wolfram Language provides users with access to their computer's file system (Files), interprocess communication (WSTP Wolfram Language Functions), evaluation of data as code (Converting between Expressions and Strings), and the ability to run arbitrary external programs (Calling External Programs). While these features enable Wolfram Language users to create powerful programs that can perform truly useful tasks, they bring with them the potential for misuse.
The Wolfram System notebook front end provides three mechanisms for evaluating code: Shift+Enter evaluations, initialization cells, and dynamic content.
Note that this tutorial contains live controls, so if you change anything it will immediately change the settings on your system.
Because Shift+Enter evaluations require user interaction to start them, the Wolfram Language provides no safeguards against potentially malicious code that is evaluated using this mechanism. Users should ensure that they do not perform Shift+Enter evaluations on code from untrusted sources. When writing their own code, users should take great care to ensure that the code does not have unintended consequences. For example, the Wolfram Language will not provide a warning when the user evaluates a program to delete files from his or her computer.
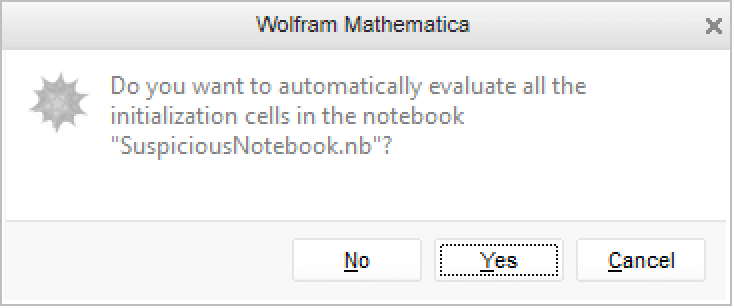
Initialization cells provide users with a convenient way to evaluate startup code needed by a given notebook when the user first evaluates any input in that notebook. Since this code will be automatically evaluated, likely without the user ever seeing the initialization code, the Wolfram Language will display an alert prompt asking the user to confirm his or her intent to run the initialization code. Users should not evaluate initialization code in a notebook that was obtained from an untrusted source unless the code has been determined to be safe.
- Clicking the Yes button will first evaluate all of the initialization cells in the notebook, then evaluate the selected cells.
- Clicking the No button will not evaluate any of the initialization cells, but will still evaluate the selected cells. Note that this may cause errors in the evaluations since they may rely on startup code that has not yet been evaluated.
- Clicking the Cancel button will cause neither the initialization cells nor the selected cells to be evaluated.
The Wolfram Language has amazing dynamic interactivity features. Notebooks containing interactive Dynamic content can automatically evaluate code without any additional action by the user, aside from opening the notebook file. Many times this is exactly what the user will want, while other times the user should be alerted before this sort of automatic evaluation takes place.
When the user opens a notebook containing dynamic content, the Wolfram Language will first determine whether the notebook's directory is trusted, untrusted, or neither.
- If the notebook's directory is trusted, the notebook will be allowed to automatically perform dynamic evaluations without alerting the user.
TrustedPath
The value of the TrustedPath option is a list of directories that are always trusted by the Wolfram Language. Any notebook file located in any directory in TrustedPath is trusted by the Wolfram Language. The Wolfram Language will never display an alert when a trusted notebook is opened, and the notebook can automatically perform dynamic evaluations.
By default, the TrustedPath option value contains $InstallationDirectory, $BaseDirectory, and $UserBaseDirectory so that Wolfram System installation files and additional installed applications will be able to display dynamic content without alerting the user.
UntrustedPath
The value of the UntrustedPath option is a list of directories that are always untrusted by the Wolfram Language. Any notebook file located in any directory in UntrustedPath is untrusted by the Wolfram Language. The Wolfram Language will always display an alert when an untrusted notebook is opened and attempts to perform dynamic evaluations.
By default, the UntrustedPath option value contains the user's desktop folder (where web browser downloads are likely to be stored), the user's configuration folder (where email attachments are likely to be stored), and the computer's temporary directory. If the user has configured his or her web browser or email program to save downloaded files in nonstandard locations, then the user is encouraged to add these locations to the UntrustedPath option value.
Nesting
Directories in TrustedPath and UntrustedPath can be nested. A notebook is trusted if the most deeply nested directory containing the notebook is trusted. Consider the following example:
- FrontEnd`FileName[{$HomeDirectory, "Desktop"}, "SomeDownload.nb"] would be untrusted because "Desktop" is untrusted.
- FrontEnd`FileName[{$HomeDirectory, "Desktop", "SafeNotebooks"}, "MyNotebook.nb"] would be trusted because "SafeNotebooks" is trusted.
TrustByDefault
The TrustByDefault option determines whether the Wolfram Language should display an alert when the user opens notebooks with dynamic content whose containing directories are neither trusted nor untrusted. Below are the possible values for the TrustByDefault option.
| True | a notebook which is not located in a directory in UntrustedPath is considered to be trusted and will not display an alert when opened |
| False | a notebook which is not located in a directory in TrustedPath is considered to be untrusted and will display an alert when opened |
| Automatic | a notebook which is not located in any directory in either TrustedPath or UntrustedPath will display an alert when opened only if the notebook contains unsafe dynamic content (see below) |
Unsafe Dynamic Content
- uses File operations
- uses interprocess communication via WSTP Wolfram Language Functions
- uses data as code by Converting between Expressions and Strings
- uses Namespace Management
- uses Options Management
- uses External Programs
Changing Option Values
TrustedPath, UntrustedPath, and TrustByDefault are options in the NotebookSecurityOptions category. They can be changed using the "Preferences..." dialog or the "Option Inspector...".
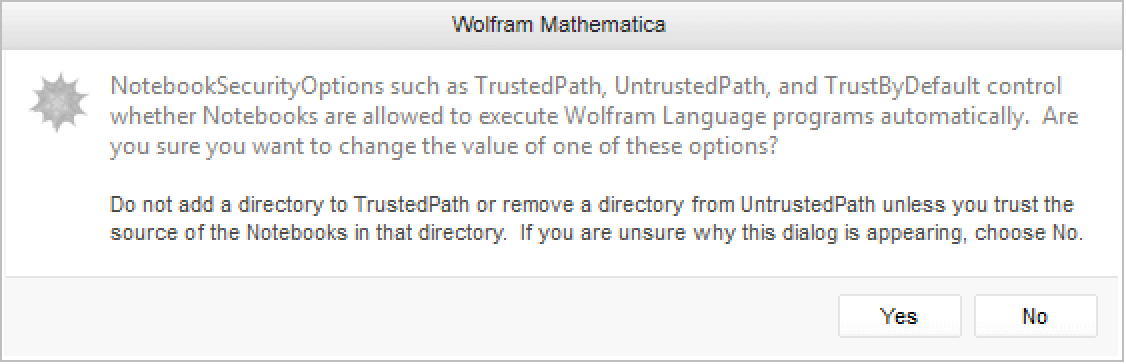
Any attempt to change the value of the TrustedPath, UntrustedPath, or TrustByDefault options will cause the Wolfram Language to prompt the user to confirm the change. The Wolfram Language does this as a security precaution so that malicious code cannot change the value of these options without the user's knowledge.